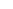This year has brought unparalleled changes to our lives, affecting nearly every one of our industries and institutions. The field of healthcare and medical device security is no exception. As medical, pharmaceutical, and other healthcare services have had to rapidly adapt to a virtual landscape, new challenges to device and data security have followed.
This year, I had the privilege to attend the 2020 Medical Device Security 101 Conference held in New Orleans. I flew all the way from Zurich, where I am a research student at ETH Zurich. I came to the conference to learn more about current trends in medical device security and share the insights I gained with the medical device security community.
The conference, which was focused on helping attendees learn and network, gave me the opportunity to meet key representatives from the medical device security industry. The evening before the conference began, I attended a dinner sponsored by MedCrypt for speakers and organizers. Additional sponsors for the event included the University of Minnesota, H-ISAC, NetLib Security, Synopsys, and Virta Labs.
The health care industry is falling prey to cyber criminals intent on stealing patient data. Medical records are rich in lucrative patient information making hospitals prime targets for ransomware attacks similar to the massive WannaCry attack that hit Windows users last year and shut down hospitals across the UK. We spoke with Dr. Chantal Worzala last year, vice president of health information and policy operations at the American Hospital Association, to learn more about what health care organizations can do to protect themselves and their patients from cyber threats.
Given the increase in ransomware attacks over the past year, healthcare organizations are making medical device security a top priority. At this year’s Medical Device Security 101 Conference, attendees will learn how to identify their biggest security challenges and develop solutions to protect their data and their patients.
In this interview with conference co-chair Kevin McDonald, Director of Clinical Information Security at Mayo Clinic, Kevin talks about what healthcare providers can learn by attending the conference, the biggest security challenges facing healthcare today, and the two things healthcare providers can do right now to improve security and protect patients.
The Archimedes Center for Medical Device Security is pleased to announce that Bill Aerts has joined Archimedes as its deputy director. In this part-time role, Aerts will lead Archimedes’ efforts to support and guide health delivery organizations and medical device manufacturers as they work to make devices safer and more secure.
As the Internet of Things grows around us, so do the threat of cybersecurity breaches severe enough to shut down hospitals and other vital infrastructure, a Michigan Engineering professor told federal lawmakers this week.
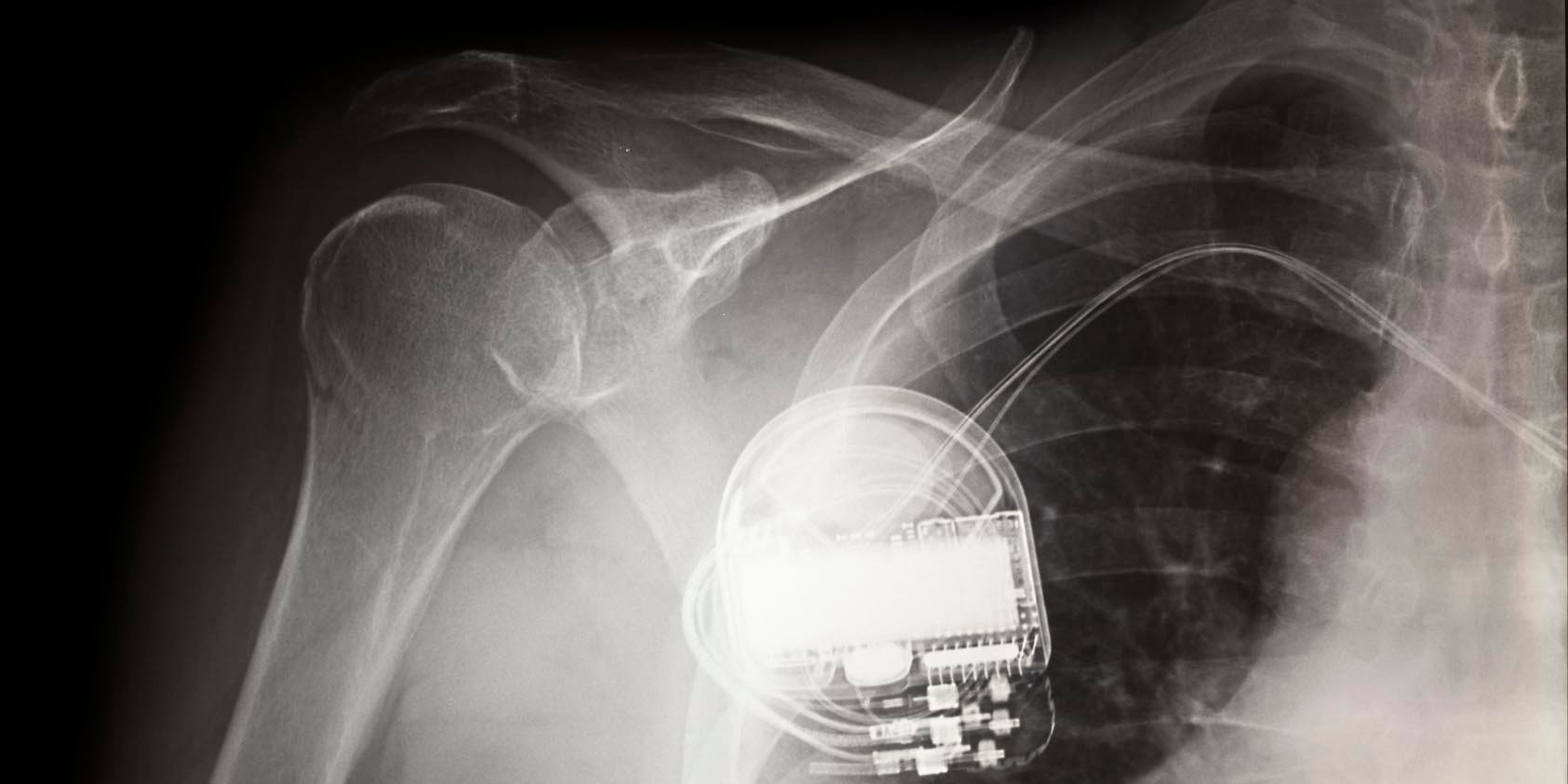
We’ve seen unprecedented attention to medical-device security after an unorthodox report was recently released by short-selling investment research firm Muddy Waters Capital and MedSec, which alleged security vulnerabilities in St. Jude Medical’s pacemakers. An independent research team subsequently raised doubts about some of the clinical claims made by the report. St. Jude Medical, meanwhile, has filed a lawsuit disputing the allegations in the same report.
St. Jude Merlin Error Indicators Are Not Evidence of Malfunction
Here’s an abbreviated technical analysis of some claims by Muddy Waters and St. Jude regarding pacemaker/defibrillator security.
Former Medtronic Director of Product Security Bill Aerts took some time recently to discuss the new security challenges arising from the IoT of medical devices, how to put together a strong security program, and the current state of medical device security (and how we can fix it).
Welcome to the inaugural Archimedes Circular Podcast. Today, Dr. Kevin Fu interviews the co-chairs of the AAMI Working Group on Medical Device Security ahead of the release of its Technical Information Report 57 to medical device manufacturers on specific security engineering methods designed to help satisfy regulatory expectations of cybersecurity in the 510(k) and PMA processes.